Security
-
What are the password requirements?
Sloneek offers three types of access security: standard password, increased password protection and MFA.
Standard password
Basic account protection that every new user of the app has. After the account is activated by the administrator, the user receives an email with a link to set their access password.
This password must be at least 6 characters long and has no expiration.
Increased password protection
If you want to take security a level further, we recommend checking the option for increased password protection in Settings / Application Settings.
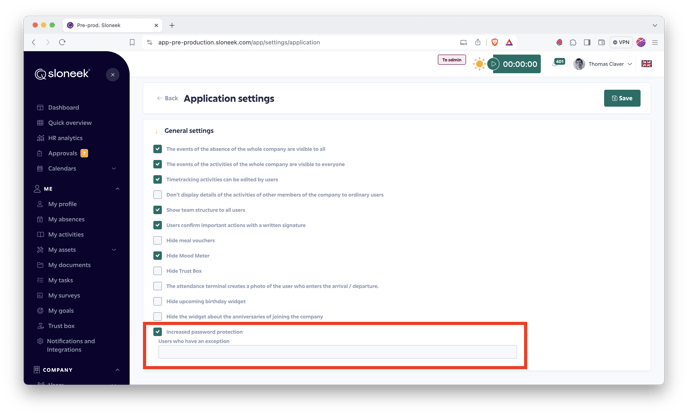
If this protection is enabled, the password must contain at least one lowercase letter, at least one uppercase letter, at least one number and at least one special character.
The password must be between 10 and 30 characters and is only valid for 60 days, after which the user must change their password or they will no longer be able to access the application.
At the same time, the old passwords are saved so that the user cannot set the same passwords over and over again. However, we only store 5 passwords in the database, so after a few interactions the first password can be set again.
MFA
MFA adds an extra layer of security to user accounts by requiring multiple forms of identification. For a detailed description and instructions on setting up MFA, see this article.
💎 The MFA service is only available for the Enterprise package.
-
Security protocol
We take the protection of your data seriously. And we do everything we can to protect it.
Access Control
Do you offer or support SAML/SSO capabilities for authentication?
- We do provide SSO only for Google Workspace and Microsoft Active Directory
What types of multifactor authentication are supported?
- We support multifactor authentication (MFA). When this option is activated by administrators, users must verify their identity by entering a code sent via SMS during the login process.
How are customer data or processes protected from unauthorized access?
- Customer data are stored at encrypted servers where there is no access from the outside world. We are using VPC (Virtual Private Cloud) where only parts of the application that are in the same network (VPC) have access to them.
What measures do you have in place to prevent unauthorized viewing of information?
- We are using JWT token (with 1-minute expiration) for authentication & authorization purposes. We are using RBAC (Role Based Access Control) in order to be able to provide customers with granularity of authorization
Who at your company can see customer data?
- Only the customer support Admins under direct and personal request granted by customer her /himself
Do you use a multi-tenant server model?
- Yes
What measures do you have to isolate individual tenant systems and data?
- Everything is mapped on an entity called “Company” and every data is associated with it via Foreign keys.
Data protection
What does your data security protocol look like? (Data security protocols, defined as “the software and behavioral rules that guide how employees handle and access data”, provide clear guidelines that demonstrate an organization’s approach to data security. This might include things like SSL certificates, virtual private networks (VPNs), multi-factor authentication (MFA), and more.)
- Customer data are stored at encrypted servers where there is no access from the outside world. We are using VPC (Virtual Private Cloud) where only parts of the application that are in the same network (VPC) have access to them.
- We are using SSL connection for all components of our application
Is your platform externally audited?
-
Yes, ISO 27001 Audited at June 2023
Do you work with other third parties to deliver your SaaS solution? If so (and if they have access to your data) then what do their security protocols look like?
- Amazon - Amazon Web Services EMEA SARL, 38 avenue John F. Kennedy, L-1855 Luxembourg, cloud infrastructure service provider. The data centres are located in Frankfurt am Main, Federal Republic of Germany.
- HubSpot Ireland Ltd, Ground Floor, Two Dockland Central, Guild Street, Dublin 1, Co. Dublin, Ireland(VAT: IE9849471F), Hubspot service for sending mass messages, newsletter and notifications (https://legal.hubspot.com/privacy-policy).
- Zendesk Inc. 989 Market Street, San Francisco, California, 94103, United States, Service for bulk messaging, notification and customer support service (https://www.zendesk.com/company/agreements-and-terms/privacy-notice/).
- Smartlook.com, s.r.o. Šumavská 524/31, Brno, CZ 60200, Czech Republic, Reg. no.: 09508830, VAT ID: CZ09508830, Smartlook for analysing user behaviour in the application. (https://help.smartlook.com/en/articles/3244452-privacy-policy)
- Stripe Technology Europe, Ltd., 25/28 North Wall Quay, Dublin 1, D01H104, ID: 0599050 Service Stripe for payment gateway services. ( https://stripe.com/en-cz/privacy)
- Google Ireland Limited, Gordon House, Barrow Street, Dublin 4, Irsko (Registration number: 368047 / DIČ: IE6388047V) - statistics services Google Analytics a Google Tag Manager. (https://policies.google.com/privacy/partners?hl=en).
- Sentry (Functional Software, Inc.), 45 Fremont Street, 8th Floor, San Francisco, CA 94105. Service for better and smart analysis of data (https://sentry.io/privacy/).
-
OpenAI Ireland Limited, The Liffey Trust Centre, 117-126 Sheriff Street Upper, Dublin 1, D01 YC43, Ireland. Service for smart analysis of data (https://openai.com/policies/privacy-policy/).
Do You Store Credit Card Information On Your Server?
- We do not store credit card information on our server. We use Stripe as a payment processor.
What happens in the event of data corruption?
- We restore them from the daily backup automatically (daily backup has isolated storage outside the application itself)
Who Owns This Data if We Stop Using You as a Vendor
- The customer owns the data
What actions do you do to destroy data after it is released by a customer?
- We delete them permanently
When was your last third-party pentest done?
- each month by the 1. day
Disaster recovery
What is/are your disaster recovery plans?
- We have automated recovery plan in comply with https://docs.aws.amazon.com/wellarchitected/latest/reliability-pillar/plan-for-disaster-recovery-dr.html
Do you perform routine disaster recovery tests?
- Yes
How often are incremental backups made?
- Every 24 hours
How many copies of data do you store and where are they stored?
- We use Amazon Web Services for backups. They are replicating back-ups to be able to achieve 100% recovery rates (https://aws.amazon.com/rds/?p=ft&c=db&z=3)
How far back do the backup copies go?
- 1 month
Have You Ever Had a Security Breach?
- No
How often and how do you test your backup and recovery infrastructure?
- Once half a year
What are your methods for backing up our data? What are offerings to back up data?
- We are backing up recurrently on daily bases all data from our databases & storage. We are using automated back-ups from https://aws.amazon.com/rds/?p=ft&c=db&z=3 to do so
Incident Response
Do you have an incident response plan?
- We have automated recovery plan in comply with https://docs.aws.amazon.com/wellarchitected/latest/reliability-pillar/plan-for-disaster-recovery-dr.html
Do you include customers in the incident response process?
- Yes
Do you provide reports of attempted or successful breaches of systems, impacts, and actions taken?
- If requested by the customer
Which tasks and incidents remain under the responsibility of the customer?
- If the incident of losing data is caused by the customer itself, it’s the responsibility of the customer. All application is covered by an Audit-Login, which stores details such as:
- IP address of the executor (person who executes an action)
- Action name
- Unique identifier of logged-in person (email)
- Timestamp of an action
- Which version of the application has been deployed at the time of the action
- Which data has been changed and eventually even the diff, what’s been changed to what
Physical Security
How do you assess your employees’ security understanding?
- We don’t have physical servers
Where is your data center, and what physical security measures are in place?
- We use datacenters located in Frankfurt provided by Amazon Web Services. We don’t have access to them
What countries is data stored in - both on your infrastructure and for backups?
- Frankfurt datacenters provided by Amazon Web Services
Regulatory Compliance
Do you comply or plan to comply with privacy regulations (e.g. Privacy Shield, GDPR)?
YES, fully comply.
GDPR
How do you collect personal data?
The subject collecting personal data is the customer (company), which collects and processes personal date of their respective employees.
Why do you collect personal data?
Personal data that are collected by subjects specified above are collected for the sole purpose of managing Human Resources agenda of the employer (company).
What are you using personal data for?
Collected personal data enables employers to plan vacations, schedule shifts, distribute internal documents and process other internal agendas.
How long will you keep the personal data?
As the owner of the data is the employer, the data will be kept in the application storage as long as the customer keeps them. In case of the customer stopping using the application, all data will be erased within 1 month after expiration of the commercial licence.
Do I have any rights?
All users, whose personal data is collected, are guaranteed all the right based on the GDPR regulation, specifically the right to observe, update, and forget.
-
Open AI at Sloneek
At Sloneek, we are committed to the highest standards of data privacy and security, especially in the context of our Human Resource Information System (HRIS).
We understand the importance of protecting personal and sensitive data, and we want to assure our users and stakeholders about our practices in this regard. We have integrated OpenAI's ChatGPT technology into our HRIS system to enhance its capabilities and provide advanced features to our users. However, it is crucial to highlight:- Strict Compliance with GDPR & ISO27001: We adhere strictly to the General Data Protection Regulation (GDPR) guidelines. Our integration with ChatGPT is designed in a way that fully complies with these regulations.
- No Sensitive Data Transmission: We do not transmit any GDPR-relevant or other sensitive personal data to the OpenAI ChatGPT API. Our use of this technology is limited to enhancing system functionalities without compromising user data.
- Data Processing Transparency: We maintain complete transparency in how we process and handle data. Our system's interaction with ChatGPT is confined to non-sensitive, operational data that does not breach privacy or confidentiality.
- Security Measures and Protocols: Our system incorporates robust security measures and protocols to protect data integrity and prevent unauthorized access or data breaches.
- Continuous Monitoring and Updates: We constantly monitor our systems and regularly update our security practices to align with evolving data protection laws and standards.
We assure all our users and stakeholders that safeguarding your data is our top priority. We are committed to maintaining the trust you place in our technology and services.
Thank you for your continued trust in Sloneek.